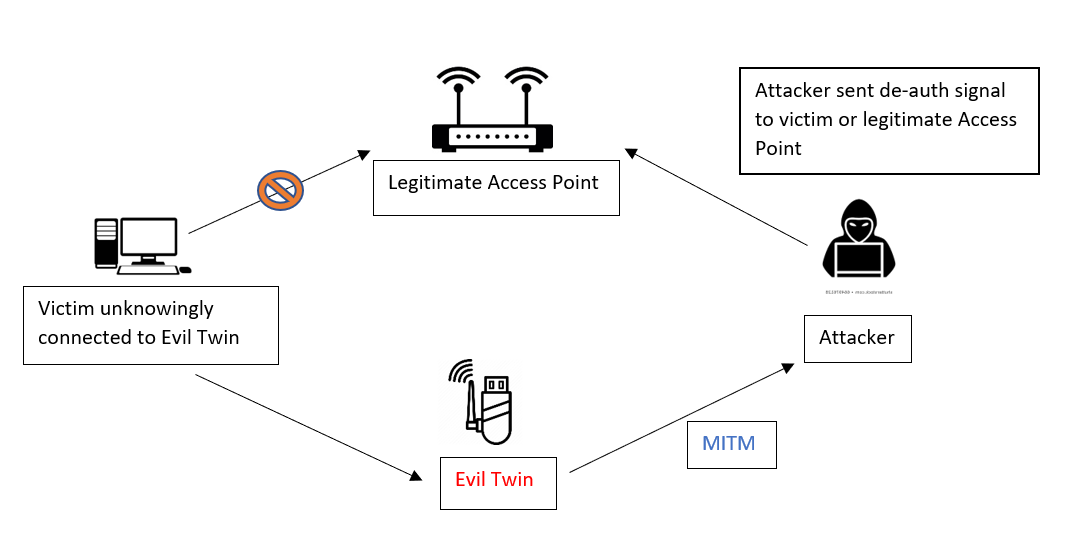
An Efficient Scheme to Detect Evil Twin Rogue Access Point Attack in 802.11 Wi-Fi Networks | SpringerLink
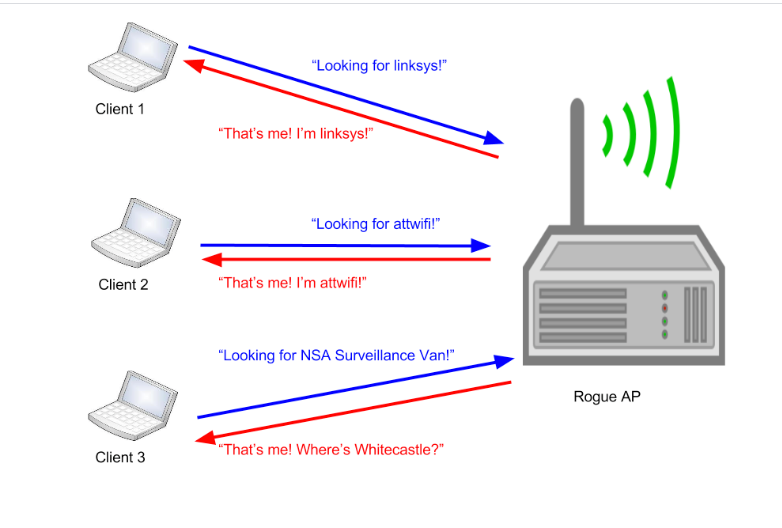
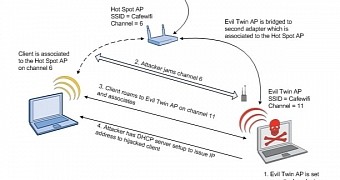
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members



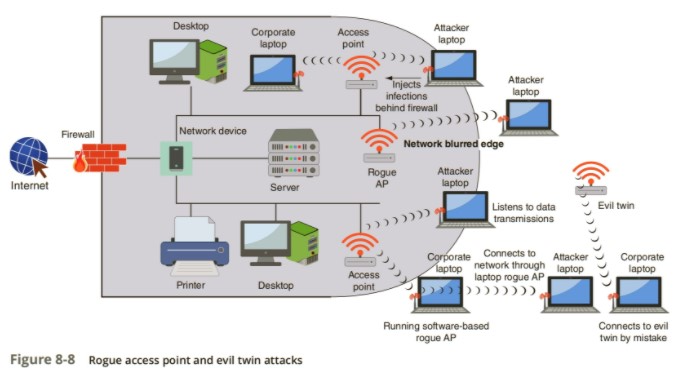
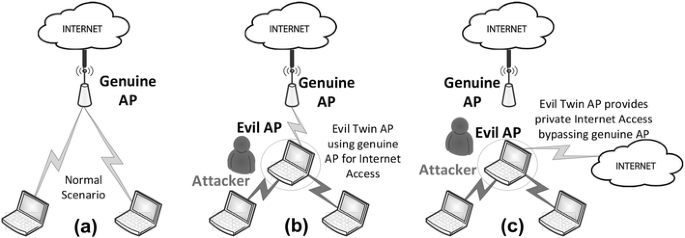
![PDF] A Flexible Framework for Rogue Access Point Detection | Semantic Scholar PDF] A Flexible Framework for Rogue Access Point Detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5f7a2fec5198aa5b1f3c846b4db50aec4dff4e3b/29-Figure2.2-1.png)