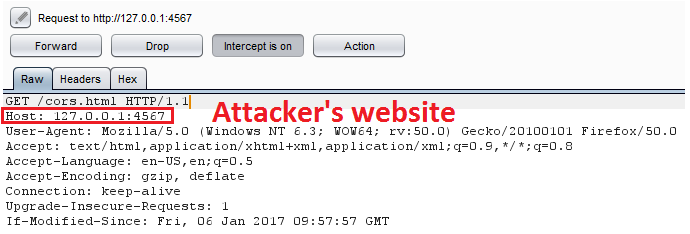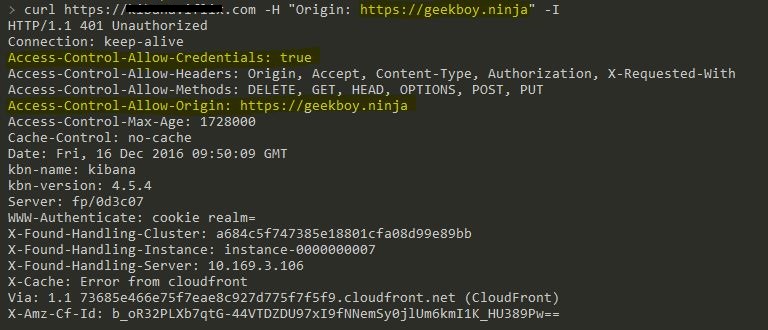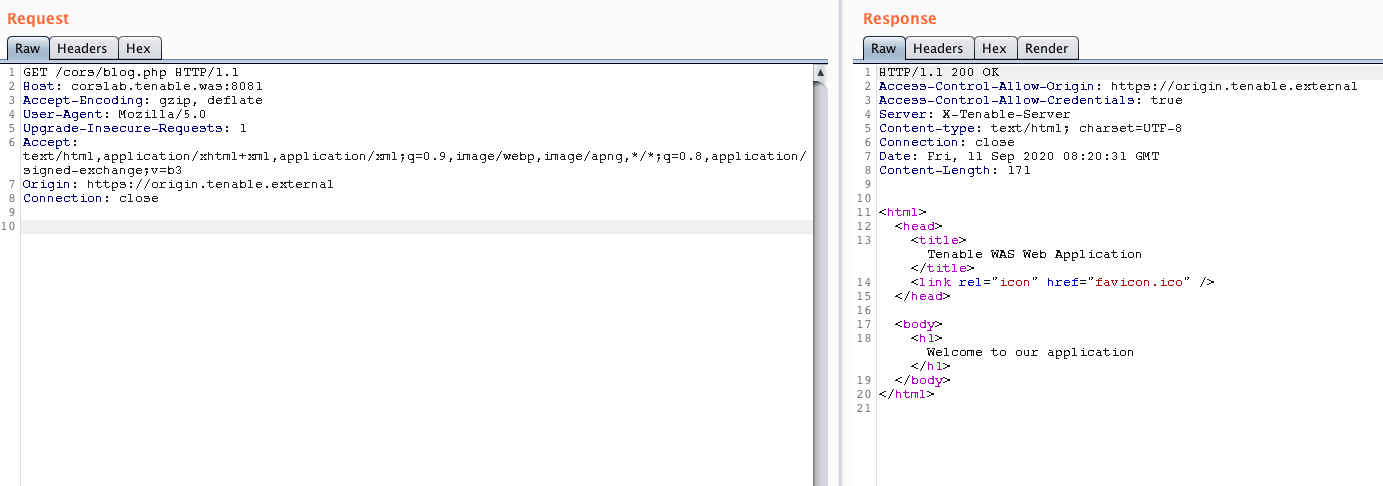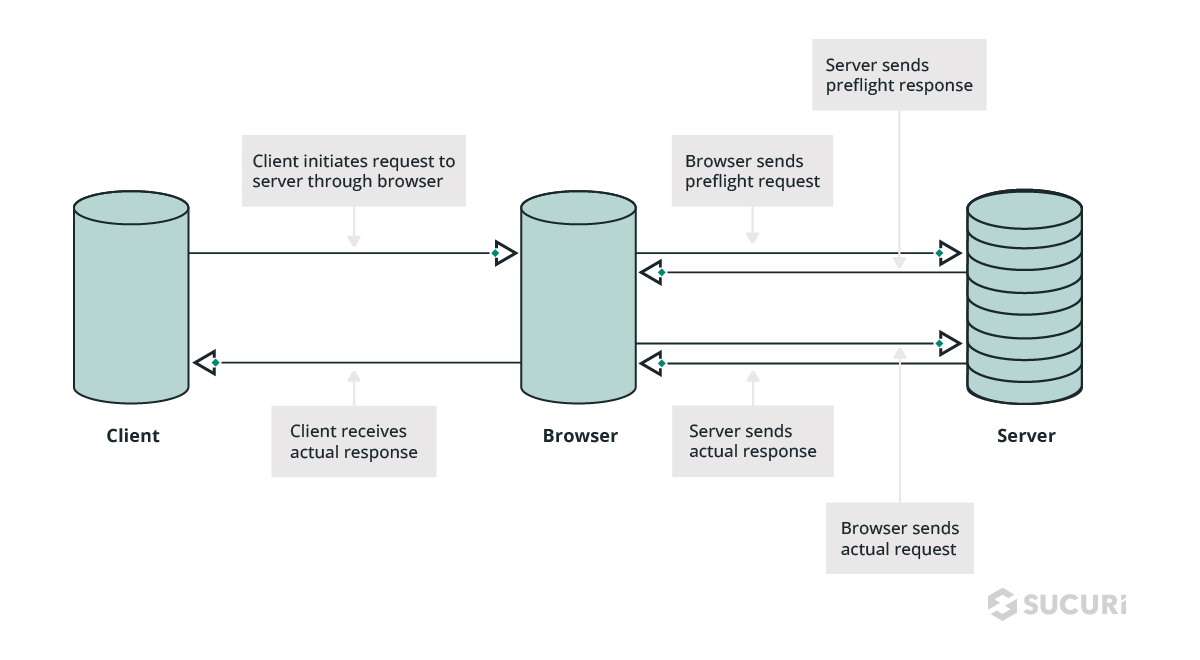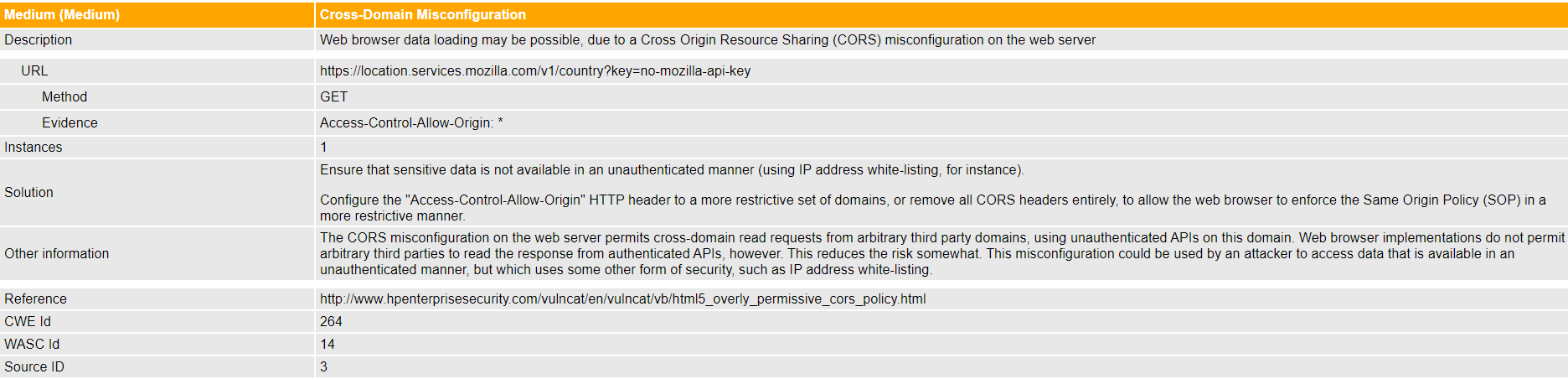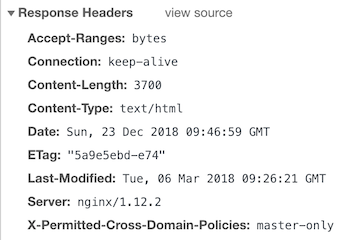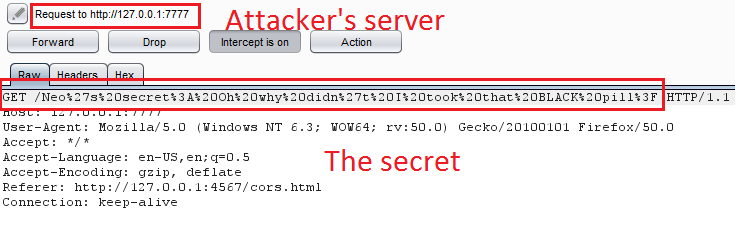
OWASP TOP 10: Security Misconfiguration #5 - CORS Vulnerability and Patch - Penetration Testing and CyberSecurity Solution - SecureLayer7

OWASP TOP 10: Security Misconfiguration #5 - CORS Vulnerability and Patch - Penetration Testing and CyberSecurity Solution - SecureLayer7
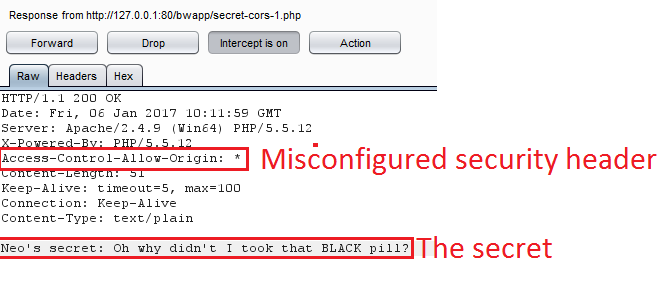
OWASP TOP 10: Security Misconfiguration #5 - CORS Vulnerability and Patch - Penetration Testing and CyberSecurity Solution - SecureLayer7