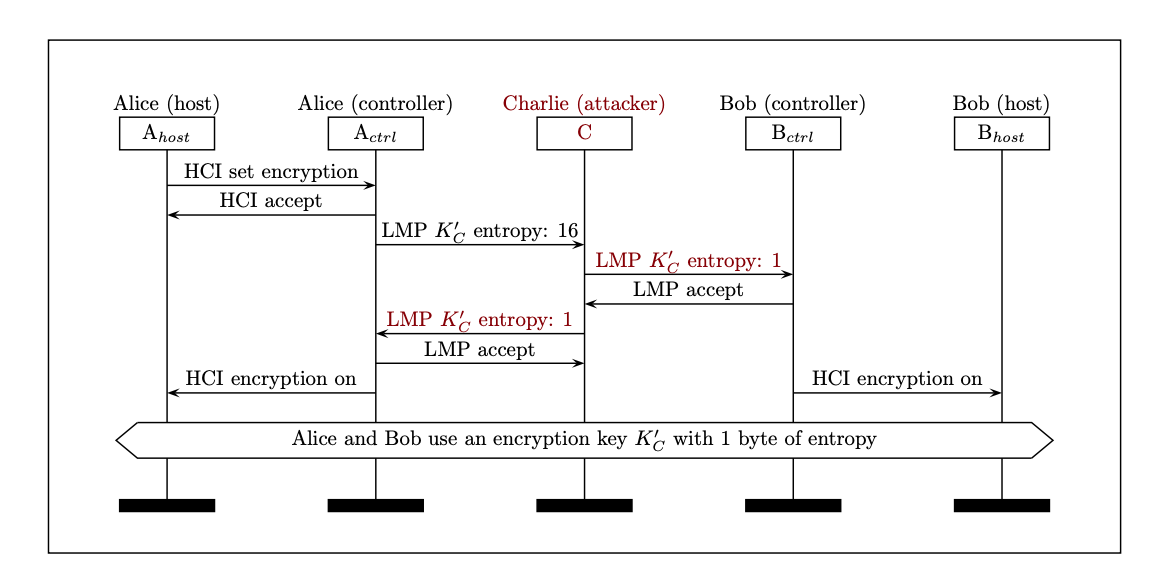
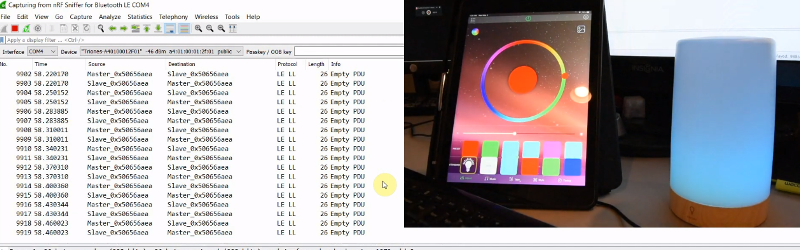
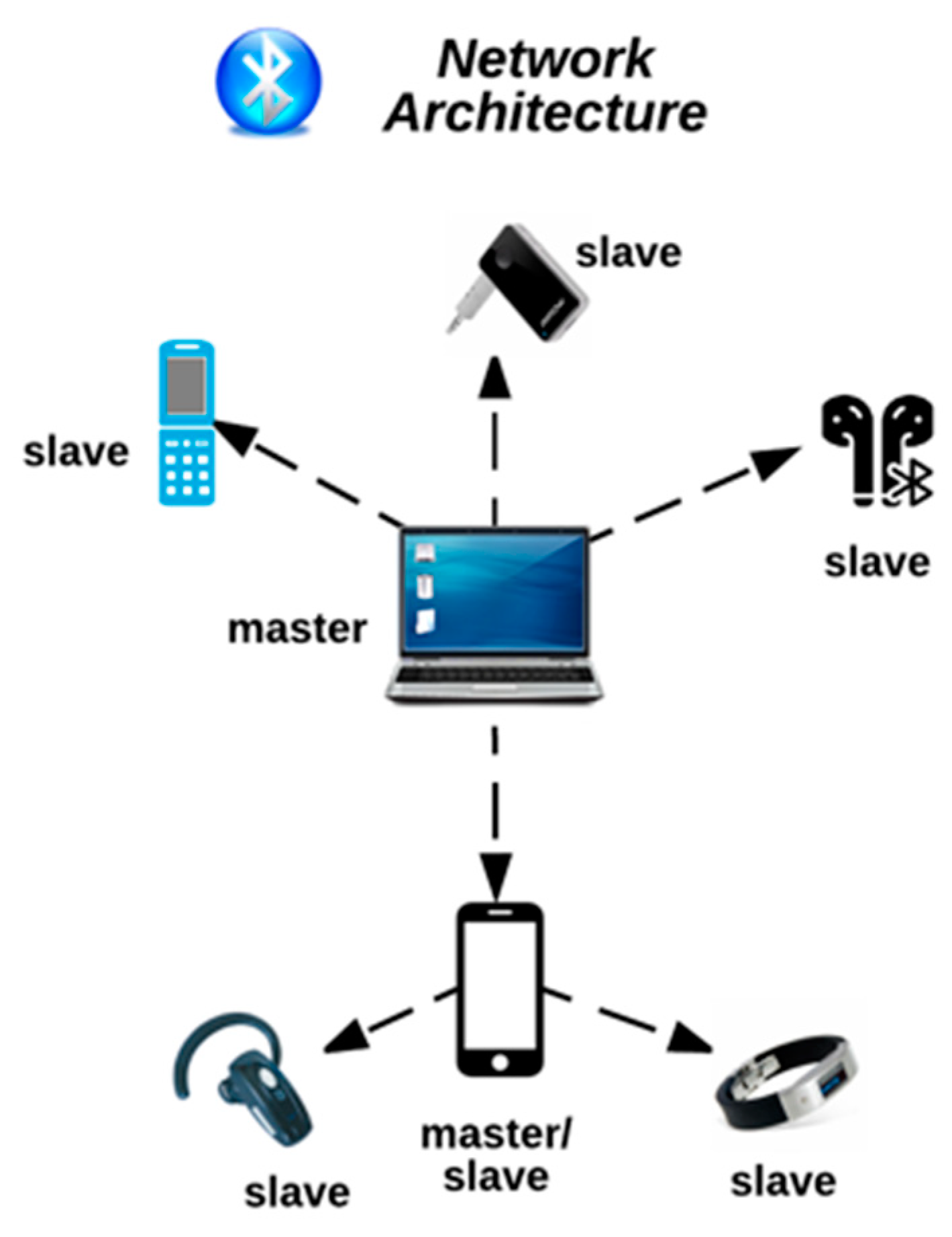
Bluetooth security flaw could allow hackers to intercept your private data | Technology News,The Indian Express

Buy Wireless Bluetooth Earphones for Samsung Intercept, Samsung J150, Samsung J210, Samsung J750, Samsung L170, Samsung L700, Samsung L810v Steel Earphones Original Like Wireless Bluetooth Neckband Flexible In-Ear Headphones Headset With Built-in

An attack-defense tree based on interception attacks on a Bluetooth IoT... | Download Scientific Diagram

Detector for Wireless Analogue & Digital Transmissionen Protect 1206I Detection – FM GSM/DECT, Bluetooth, WLAN/Bug Finder/Detector/102B Device: Amazon.de: Electronics & Photo
Drill-down... Bluetooth UART Interception on Embedded Artists Dev Kits | Community | Murata Manufacturing Co., Ltd.
![How to intercept the bluetooth joystick button press when the screen is locked. - Cross-platform - Delphi-PRAXiS [en] How to intercept the bluetooth joystick button press when the screen is locked. - Cross-platform - Delphi-PRAXiS [en]](https://en.delphipraxis.net/uploads/monthly_2023_01/S_member_10894.png)
How to intercept the bluetooth joystick button press when the screen is locked. - Cross-platform - Delphi-PRAXiS [en]