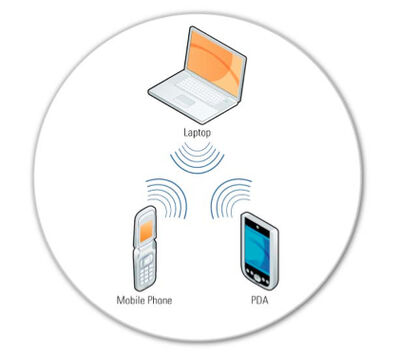
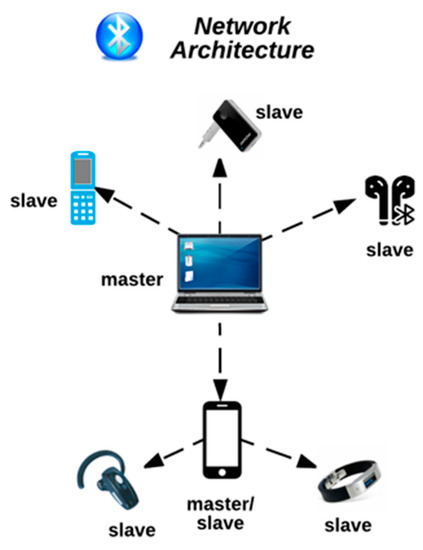
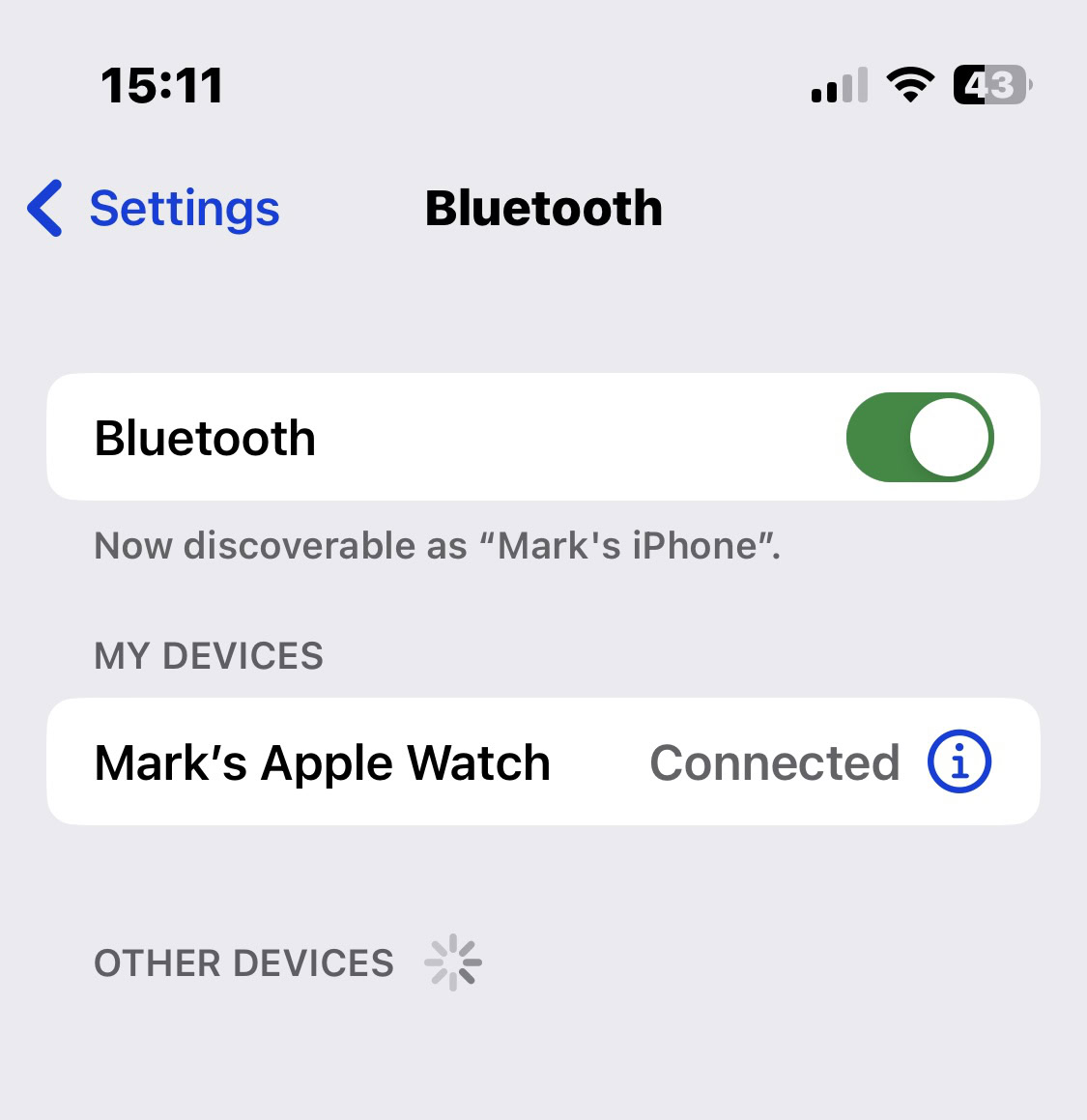
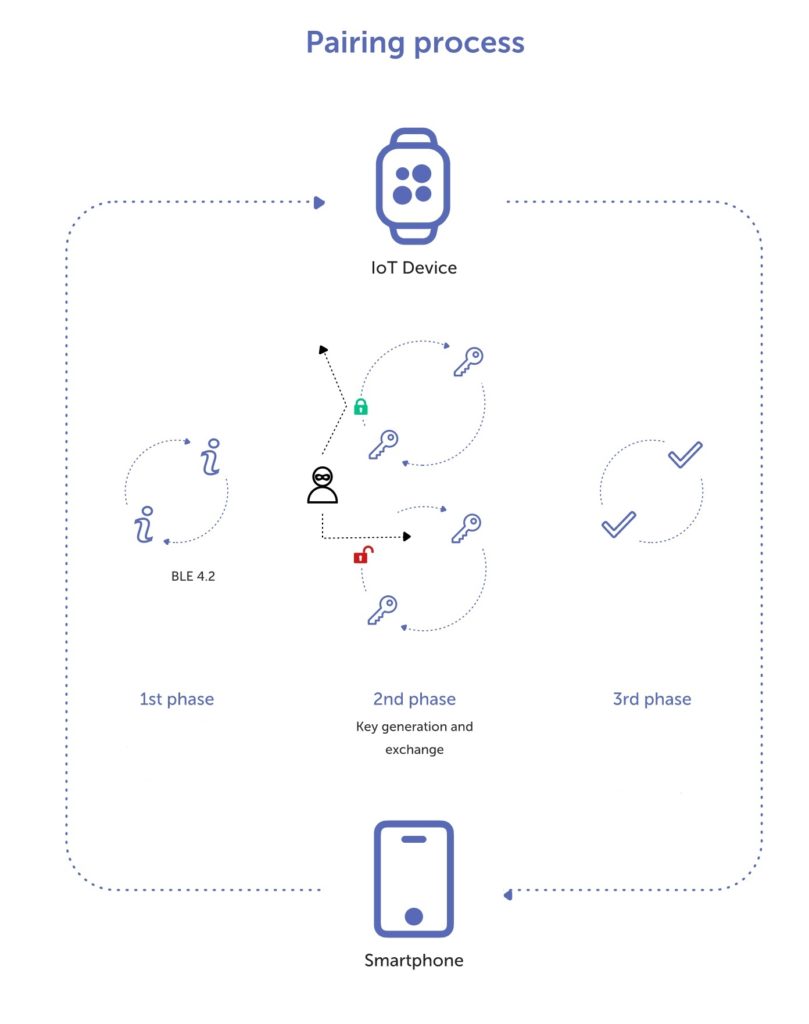
Wi-Fi Man-in-the-middle Attack Eavesdropping Wireless Bluetooth PNG, Clipart, Bluetooth, Brand, Cracking Of

Protect 1207i - Leistungsfähiger Wanzendetektor - abhörgerät aufspüren / GSM, CDMA, 3G, DECT, Bluetooth, WLAN und WiMax: Amazon.de: Elektronik & Foto

Bluetooth: Operation and Use (McGraw-Hill Telecom Professional) (English Edition) eBook : Morrow, Robert: Amazon.de: Kindle-Shop