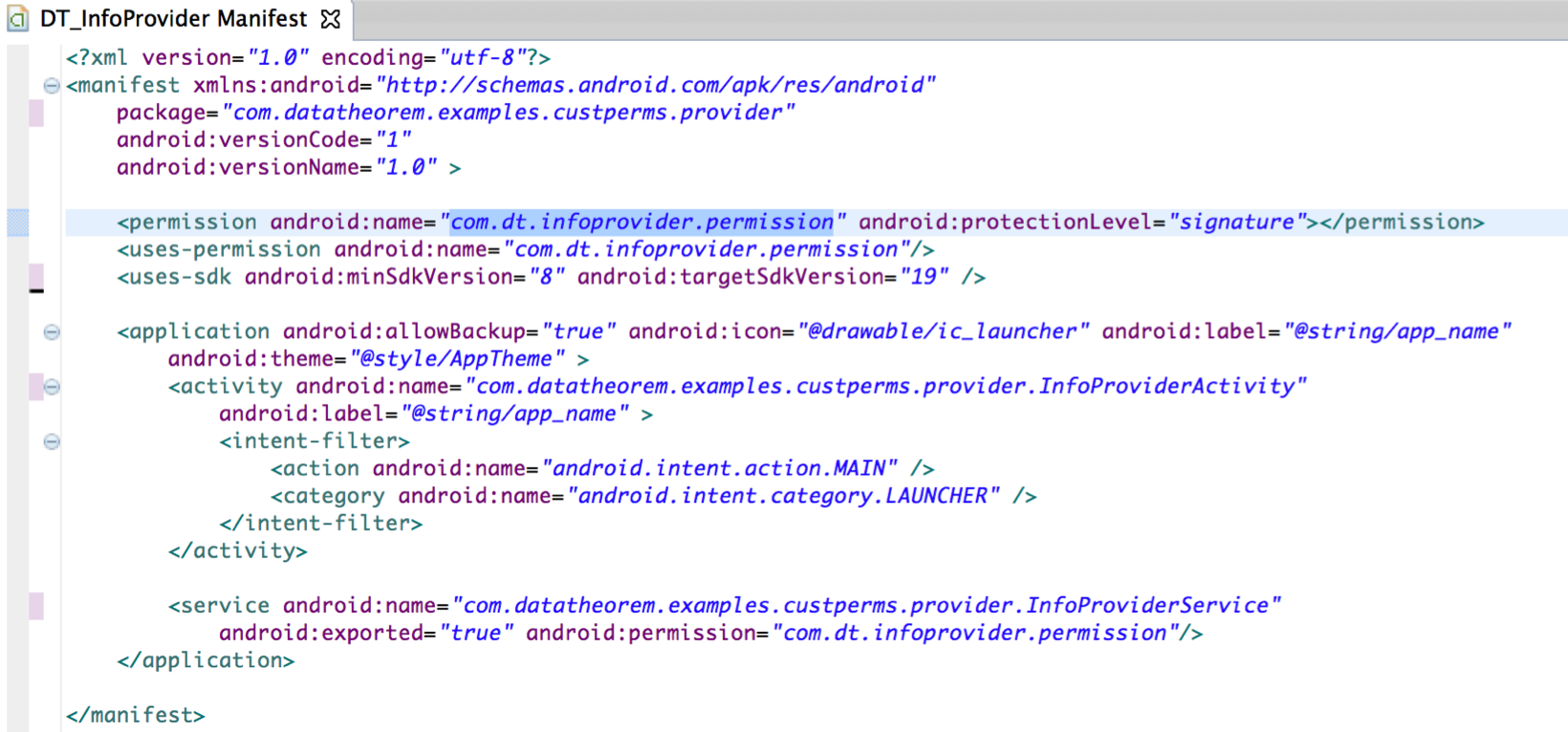
5. How to use Security Functions — Android Application Secure Design/Secure Coding Guidebook 2020-11-01 documentation

google cloud messaging - Can I remove this permission? (It cause INSTALL_FAILED_DUPLICATE_PERMISSION in Android 5.0 device) - Stack Overflow

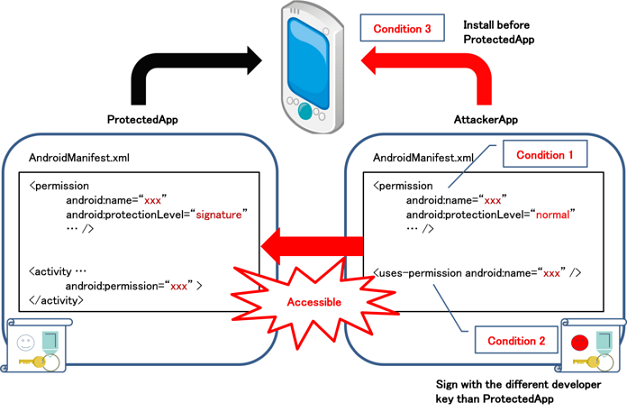
Protection level flags and permission flags of Android Permission System. | Download Scientific Diagram
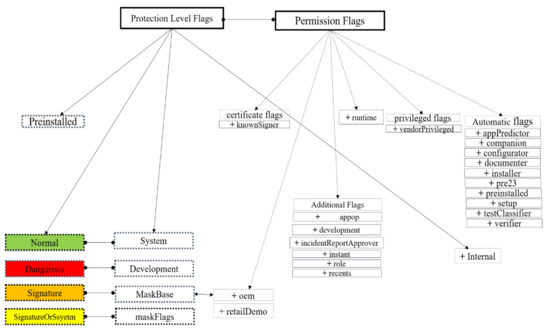

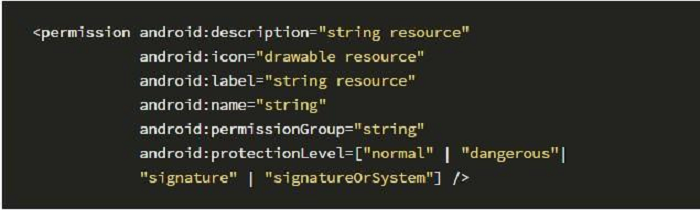

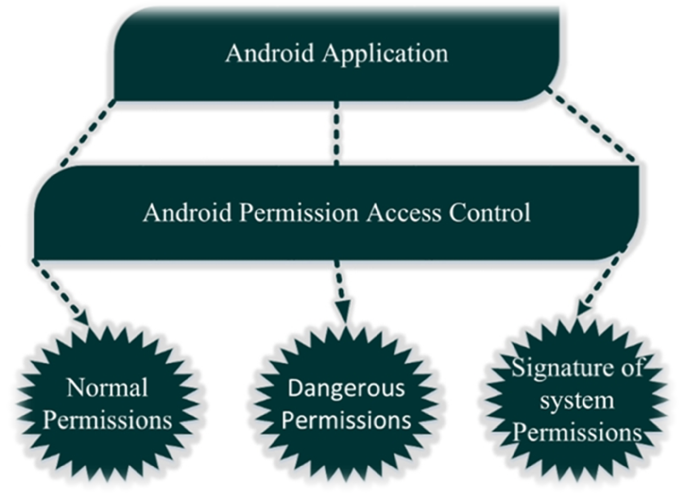
![PDF] A Comprehensive Analysis of the Android Permissions System | Semantic Scholar PDF] A Comprehensive Analysis of the Android Permissions System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e6f3bf70f29c154790c93281a4b1b6c64ac9f6bc/6-Table3-1.png)

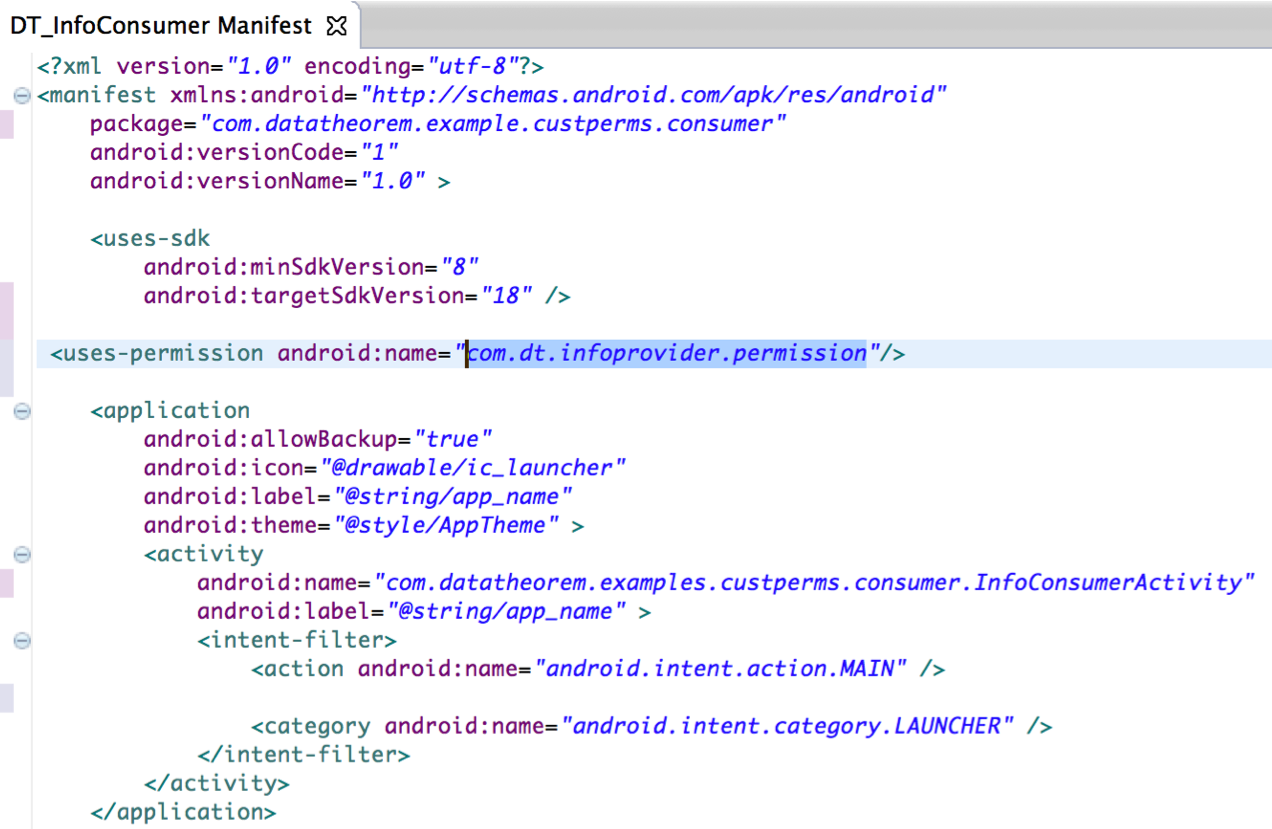

![PDF] A literature Review on Android Permission System | Semantic Scholar PDF] A literature Review on Android Permission System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4ff5fbb7191b4d76d9fbb2abbbd8d503c98acfac/2-Figure3-1.png)





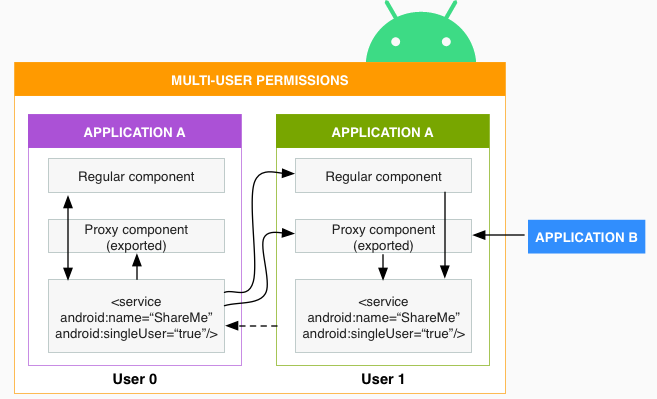
![Android Runtime Permissions[Updated with Android 11] Android Runtime Permissions[Updated with Android 11]](https://www.howtodoandroid.com/wp-content/uploads/2022/03/Camera-run-time-permission.png)