0xor0ne on Twitter: "Linux kernel exploitation intro series by Keith Makan Debugging: https://t.co/MFkoXhjCXP Stack overflow: https://t.co/JyCPAttO1V Privilege escalation: https://t.co/mIdgQs4F0f #Linux #kernel #exploit #infosec #cybersecurity https ...

0xor0ne on Twitter: "Linux kernel exploitation intro series by Keith Makan Debugging: https://t.co/MFkoXhjCXP Stack overflow: https://t.co/JyCPAttO1V Privilege escalation: https://t.co/mIdgQs4F0f #Linux #kernel #exploit #infosec #cybersecurity https ...

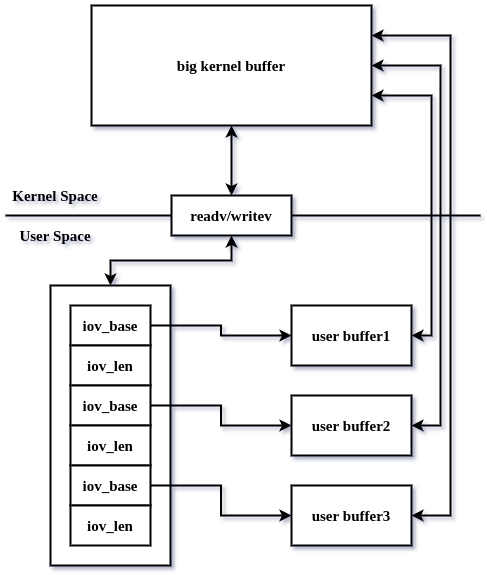
Abhisek Datta on Twitter: "Root cause analysis of CVE-2019-2215 #Android #BadBinder by @HackSysTeam Documentation here https://t.co/yTQVZLOlRZ https://t.co/C0FaDOai9V" / Twitter

Buy A Guide to Kernel Exploitation: Attacking the Core Book Online at Low Prices in India | A Guide to Kernel Exploitation: Attacking the Core Reviews & Ratings - Amazon.in

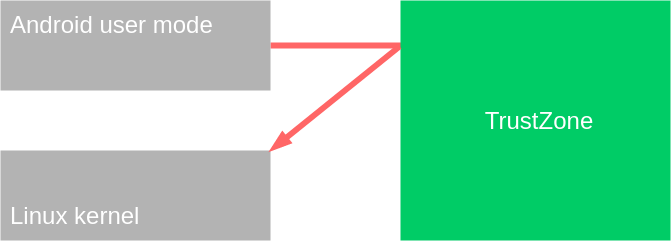
Elevating The TrustZone To Achieve A Powerful Android Kernel Exploit | Tamir Zahavi Nullcon Goa 2022 - YouTube

Buy A Guide to Kernel Exploitation: Attacking the Core Book Online at Low Prices in India | A Guide to Kernel Exploitation: Attacking the Core Reviews & Ratings - Amazon.in
GitHub - xairy/linux-kernel-exploitation: A collection of links related to Linux kernel security and exploitation

Abhisek Datta on Twitter: "Root cause analysis of CVE-2019-2215 #Android #BadBinder by @HackSysTeam Documentation here https://t.co/yTQVZLOlRZ https://t.co/C0FaDOai9V" / Twitter